Chad Hatfield clearly remembers the day he walked into his office and saw his wife preparing to transfer funds from the company’s bank account. “What are you doing?” he recalls asking. His wife answered that she was transferring money—as Hatfield had requested in an email to the company’s office manager.
But Hatfield had written no such email. Instead, it turned out, his Dallas-area company, Hatfield Builders & Remodelers, had been the victim of a cyberattack.
Seventy-one percent of data breaches occur in businesses with fewer than 100 employees, according to a study by Verizon. This isn’t because criminals can make a huge profit by stealing from them; it’s because automation allows them to attack thousands of family-owned businesses at the same time, and many of these firms aren’t well-protected.
In Hatfield’s case, his office manager had received an email and clicked on what she thought was a Dropbox link. That installed a virus, which gave someone in Nigeria access to her email account. The attackers then deleted all new emails between Hatfield and the office manager, and wrote one of their own, claiming to be Hatfield and asking the office manager to transfer $8,000 to a client’s bank account in North Dakota.
“She tried to do it, but you needed a two-person authorization to transfer money at our company,” Hatfield says. That’s how his wife got involved. Today, no one wires money out of the business at all.
Perils of Connectedness
Another factor that adds to the vulnerability of smaller companies is interconnectedness. Today, more and more businesses rely on networks that provide interaction with customers and vendors. Some believe that this makes them not only a target, but also a springboard to a more lucrative prize.
“As the digital world becomes more entwined, large companies are requiring vendors to interact with internal systems including procurement, marketing, human resources, [and] payroll,” says Alan Moss, a managing partner at security consulting firm Conventus. “These relationships create access into the parent organization—the ultimate target.” Moss’ comments appeared in CSO magazine.
What’s a Small Business to Do?
The first, and biggest, step you can take is to educate yourself and your staff. Add data protection policies to employee handbooks and inform all staff members about data confidentiality and common cyberattack practices.
“We get three or four emails a week in our general inbox that are bogus,” Hatfield says. “They seem like real leads. Someone will write, ‘Hey, I want to redo my kitchen and I’ve got some initial thoughts. Can you open these pictures and then give me a call?’” (See sample email from Hatfield, below.)
Always keep systems and software updated. Utilizing the newest version of any online system means you are up to date with any updates made to combat recently discovered vulnerabilities.
Finally, take a look at your passwords. Most data breaches are the result of weak or stolen credentials, according to Verizon’s Data Breach Investigation Report. Consider a system such as LastPass or Google Authenticator to strengthen password security.
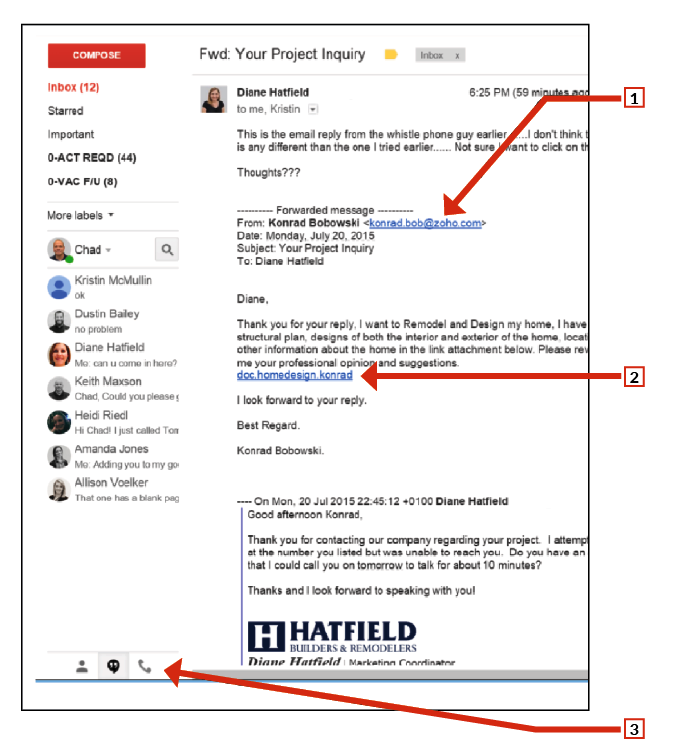
1] Is the email from a provider you recognize, such as Gmail? You can also hover your mouse over the address itself and the real address will appear in the lower left of your screen. In this case, the email is from Zoho.com, a Russian company. Not a likely client.
2] Here, Hatfield is being asked to look at a project, but if you hover your mouse over this link, the name doesn’t match the actual link, which is in Vietnam.
3] The real website link will appear here. Don’t click the link! This email is phishing.
In today's interconnected online world, businesses are vulnerable, and businesses with fewer than 100 employees even more so
Add new comment
Related Stories
Brian Gottlieb Receives Remodeling Mastery Award
Presented by industry icon, Mark Richardson, the award celebrated Gottlieb’s extraordinary impact on remodeling
What's Beyond the Hammer?
Working with Brian Gottlieb on the book Beyond the Hammer provided a masterclass on how to build an aligned team
Real AI Applications For Remodelers
Tech-forward remodeler Michael Anschel shares how he uses artificial intelligence in his business.
How to Eliminate Boring, Languishing Meetings
Leff Design Build ensures maximum productivity and efficiency through these straightforward methods
5 Counterintuitive Strategies to Improve Your Business
Follow these strategies to inspire employees, instill trust, and beat the competition
Couple Act As Much More Than General Contractors
How LBR Partners uplifts and educates their Spanish-speaking trade partners
How to Train for and Run Effective Design-Build Meetings
On this episode of Women at WIRC, Morgan Thomas of LEFF Design Build shares how to maximize your time by creating a culture around effective, collaborative meetings
Pro's Picks: A Real-Time Project Communication and Management Tool
This remodeler says this product allows for easy, quick, real-time communication with team members in the field and in the office
How to Create a World-Class Remodeling Team
Great remodeling companies position themselves for the future with the right players
Everyone Should Have a Number: KPIs for Your Design Build Team
Measuring key performance indicators guides your team to success while creating accountability and ownership